It’s no surprise that Arm64 PCs hit a sweet spot for music creation and live performance. They are thin and light, have excellent battery life (I used a Surface Laptop 7 at the entire NAMM show and never had to charge it despite giving presentations and demos), great screens, USB-4 ports that support Thunderbolt 3, and are super quiet. They continue to get even more powerful, as seen during Snapdragon Summit this year with the announcements around Snapdragon X2 Elite, including the 18 core, 5 GHz Snapdragon X2 Elite Extreme.
The Snapdragon X Elite Arm64 PCs have impressed me so much over the past year and a half, not only with the hardware but the software compatibility, that I didn’t even hesitate before picking one for my daughter this past September to bring to college. The only difficult choice we had to make was the color (Surface Laptop 7 in that gorgeous Sapphire Blue).
Although my huge water-cooled coal-burning desktop is an Intel 285k beast with 192GB memory and 16TB of storage, that I could not part with, I really appreciate everything Arm brings to the table when I use my travel PC running a Snapdragon X Elite processor. And most people today purchase laptops, not desktops.
For those who prefer a laptop as their primary PC, Windows Arm64 devices are a great choice because of all the above reasons, and they have great screens and device connectivity. It was great to present at the MIDI association events at NAMM, running a full DAW workload on the laptop, while having it sitting on my lap without sending me to the burn unit. No fan blowing on the folks sitting next to me, no noise for my mic to pick up, no heat on my laptop, and best of all, no problem running plugins, a stand-alone synthesizer, MIDI 2.0 debug apps, and a full DAW. And did I mention that I didn’t have to run around looking for a power outlet while there?
Microsoft has been investing heavily in Arm64, and so are our development software and hardware partners. Let’s take a look at where we are for Arm64 for musicians and other audio professionals/creators, and where we’re headed in 2026.
Making Music on Windows on Arm
The past 12 months have seen huge progress in building the ecosystem around making music on Windows on Arm. Over the year, we’ve had most DAWs go fully native on Arm64 (including their in-box plugins), more plugin releases, releases of new native Arm64 drivers for audio interfaces, news about our own in-box ASIO driver, a great Qualcomm booth at the NAMM show and CES, and much more.
A huge thank you to all our partner developers out there who have made this happen!
This is a long-ish post with something for everyone. Here’s what we’ll cover:
- Arm64 Software like DAWs and software production
- Audio interfaces and the hardware ecosystem
- In-Box Low-latency (ASIO) Audio Driver for USB Audio Class 2 Devices
I briefly covered Windows MIDI Services in my most recent blog post. The team has been working really hard to fix any last-minute bugs found in our testing and our partner testing, and have been putting the results into the pipe to get into retail Windows. I’ll mostly leave that out of this post and provide more details there when we ship the production bits for both Arm64 and x64 in Q1 2026.
Software
There’s lots of Arm64 software, both native and emulated, but let’s focus on what’s critical to the musician workflow: DAWs, Plugins, and Software Protection.
Ableton Live
Ableton is a great partner with a great set of products, both software and hardware. Arm64 Windows laptops are especially well-suited to live performance, and so a perfect match for Live. At Snapdragon Summit this September, Qualcomm announced that Ableton Live will be coming to Arm64 in 2026, as a native application. They also put together a great video with a local Hawaiian artist to showcase in-development Ableton Live on an Arm64 Copilot+ PC.
See the Ableton Live keynote segment at 46:05
We’re really excited to see Ableton Live coming to Arm64 in 2026!
There are many other equally important DAWs and apps out there, starting with the launch partners for Snapdragon X Elite: Steinberg Cubase and Nuendo, and REAPER.
Steinberg Cubase and Nuendo
We appreciate Steinberg taking the early leap here and leading the way for the industry by not only being among the first on the platform, but by performing live, all day, out in the Hawaiian sun, on Snapdragon laptops. The performances Cooper and Don gave out there were fantastic, and really showcased what Cubase on Windows can do.
At the Winter NAMM show this year, Cooper and Dom once again took the stage, using Cubase on Arm64, and a preview of the upcoming in-box ASIO driver, all for live performance on the show floor.
Watch the launch video with a live guitar performance on Cubase on Windows on Arm
Behind the Beats with Dom Sigalas | Snapdragon Sound Sessions
In addition, we’d like to congratulate Steinberg on the recent license changes for ASIO and VST, making them now much more open source compatible with the new terms. Thank you, Steinberg!
Cockos REAPER
REAPER is another partner that was ready for musicians at Snapdragon Summit 2026, and an early adopter for Windows on Arm. REAPER is a well-loved application with a vibrant and supportive community. It has a very efficient audio engine, all coded at a very low level and in a cross-platform way, plus a highly customizable user interface. The engineering work that went into all that is impressive to say the least.
We Justin Frankel from Cockos as a guest on the DAWbench podcast a few years back. If you want to geek out a bit with some REAPER internals, check it out here.
Bitwig Studio
Around this time last year, Bitwig Studio went fully native on Arm64. Bitwig has been a long-time Windows and Surface partner, and early to incorporate features like touch in their UI. I remember seeing Bitwig Studio on the 28” Surface Studio folding multi-touch displays at the NAMM Show a few years back, and it looked and felt amazing. Personally, I think Bitwig Studio has one of the best-looking user interfaces for DAWs. 
Congratulations also to Bitwig on the release of the Bitwig Connect 4/12 audio interface. It’s one of the key test devices I have here for our new ASIO / USB Audio Class 2 driver and the new MIDI drivers and stack, and is a fantasic way to link together MIDI, audio, and modular CV control.
I also had a chance to try out the new Melbourne Instruments Roto-Control Bitwig Edition at SuperBooth back in May, and at the MIDI Association meetings before that, and the integration there is fantastic.
Bandlab Cakewalk Sonar and Cakewalk Next
I’ve worked with the Cakewalk team for a long time, even co-presenting with Noel Borthwick at a Build event a decade or so ago, where he walked through Cakewalk source live on stage. Cakewalk Sonar continues to move forward as a solid Windows DAW with a great fan base. It also recently went through a huge facelift, bringing a gorgeous dark-mode UI that really modernizes the application. Cakewalk Sonar is another application which has not shied away from making the most of Windows, with support for different input modalities, different audio APIs, and more. We’re excited to see all of this now available on Arm64 PCs.
See Cooper Carter on Cakewalk Sonar with THU on Windows on Arm
Fender/PreSonus Studio One and Fender Studio
Fender/PreSonus have ported to Windows on Arm, not only for the great DAW Studio One, but also a brand new app in the Microsoft Store on Windows: Fender Studio. The free Fender Studio app is a portable 16 track recorder with built-in Fender amp sims. But it’s more than just a guitar rig, you can use it to edit audio, record podcasts and overdubs, or just jam along live with backing tracks.
Fender Studio is built upon core technology from Studio One, which is another fantastic DAW on Windows, and one which I’ve recorded a bunch of pieces using. I’m excited to see both of these great apps go full native on Arm64.
Algoriddim djay Pro
At the Winter NAMM show this year, the Qualcomm booth was showing off djay Pro and its real-time NPU-powered stem separation capabilities. This is the kind of thing I love seeing AI and the NPU used for, where it helps the creator be more creative by doing some of the chores that are difficult or impossible to do otherwise.
This was a super popular demo station at the NAMM show, with everyone trying out their DJ skills and having to just pick up, with just two fingers, what has to be the lightest laptop I’ve ever used, and it was running djay Pro and its NPU-powered stem separation without breaking a sweat.
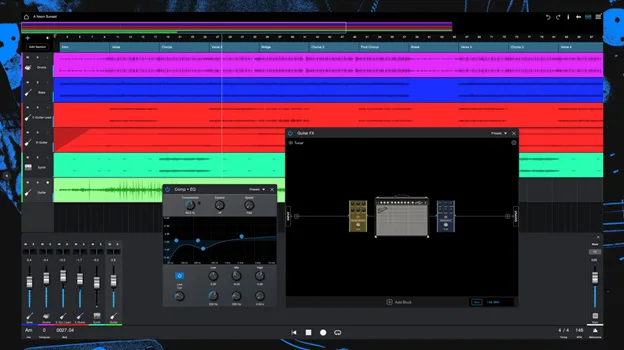
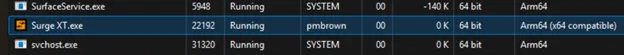
Surge XT
The free Surge XT synthesizer, originally started by Claus of Bitwig and CLAP fame, includes Arm64/Arm64EC native beta releases in their nightly builds, available on GitHub. Here’s SurgeXT running on my Snapdragon-powered Surface Laptop 7. The “x64 compatible” means it is Arm64EC, which enables integration with emulated processes/code, but is still native Arm64 code itself.
Get Surge XT here Try the nightly builds here
We recently interviewed Paul, the lead maintainer of Surge XT, on the DAWbench Podcast. This was a super fun podcast to record, and is now up at the DAWbench podcast site as well as YouTube, Spotify, Apple Podcasts, and more
JUCE
JUCE is one of the most popular frameworks for developing both stand-alone music creation apps as well as plugins supporting all the popular formats. They’ve had Windows Arm64 support for quite some time (Surge XT uses it, for example). Recently, PACE announced JUCE support for MIDI 2.0, including Windows MIDI Services, in their preview branch. This means JUCE will be ready for MIDI 2.0 on Windows as soon as we release it!
iLok / PACE Software Protection
Last, but certainly not least, is iLok. Or, to be more precise, the full suite of software protection products that PACE Anti-Piracy, Inc provides. As an end user, we usually only see the iLok tools themselves, but there’s much more to it, starting at the app/plugin compilation stage. To support Arm64, all of that technology needs to be ported. What ultimately we see as iLok is the end of a long chain designed to help software developers protect their investments and continue to create great software for musicians.
When we checked in with PACE, here’s what Neal Michie recently had to say about Arm64 support:
“PACE has delivered an initial beta release of its next-generation software protection to developer partners. This release introduces Arm64 support. Throughout 2026, PACE will extend Arm64 support across its full suite of products, including iLok for software licensing.” – Neal Michie – VP of Product Management, PACE Anti-Piracy, Inc.
So I’m really excited to see that coming! Software protection is a reality, especially in the plugin world, and native Arm64 versions will help unblock those developers who use PACE’s suite of tools. If you are a plugin developer this is great news for you so you can begin or finish your port to Arm64.
Other Software
There are some other popular DAWs that are blocked by their compiler technology at the moment. We’re working with those compiler teams to bring up full support for Arm64 in 2026 to help unblock these apps.
There are many other software releases including native Arm64 ports, and also optimizations to ensure apps run really well under emulation on Arm64 devices. For example, both FL Studio and Reason Studio work great under emulation. Because of the investment in the Prism emulator, in many cases, the emulated software can run nearly as well as native, but uses more battery.
Obviously plugins are an incredibly important part of this ecosystem. We’ve heard from plugin developers that many of them are working towards Arm64 support on Windows over the next calendar year. Still others can often be run under emulation in DAWs which support mixed-architecture plugin loading.
Hardware
Class-compliant MIDI devices will just work with the Windows MIDI Services stack when we release it in Q1 2026, for both x64 and Arm64. For modern MIDI devices, you generally do not need to use a third-party driver because our new code is all multi-client, performs well, and supports both MIDI 1.0 and MIDI 2.0 devices.
Beyond MIDI, audio interfaces are another area where vendor drivers are even more common (to the point of being required today to get low-latency performance). More on our approach that in a moment, but first I’d like to celebrate all the great devices out there today, complete with native Arm64 drivers.
Steinberg/Yamaha interfaces
Steinberg / Yamaha were launch partners for music creation on Snapdragon in 2024. And they’ve continued to be great partners since then. They have released, and continued to maintain, their Yamaha Steinberg USB Driver for the full set of models listed on their driver release page.
Steinberg also deserves credit for working with us to support Microsoft using the ASIO SDK in Windows for the new UAC2/ASIO driver Yamaha is building with us. Thank you to both Steinberg and Yamaha!
RME audio interfaces
In early 2025, RME released native Arm64 support for their entire line of USB Audio Class 2 devices. RME makes fantastic high-end devices (my home PC uses an HDSPe MADI FX) with stable low-latency drivers. Thanks again to RME for taking the plunge early and making so many devices available for Arm64!
Focusrite interfaces
This summer, Focusrite released native Arm64 support for their entire line of USB Audio Class 2 devices. You can’t miss the red (and a limited-edition blue) boxes out there. You see them on musician desks, podcasts, gamers, and more. Focusrite makes some of the most popular audio interfaces on Windows.
Focusrite USB Audio Interfaces
Audient iD series interfaces
Just after Snapdragon Summit last year, Audient released native Arm64 support for their iD series of USB Audio Class 2 devices, providing native Arm64 support for their family of popular interfaces.
In-Box Low-latency USB Audio Class 2 and ASIO Driver
We applaud all of these partners for releasing great native Arm64 support. A native vendor driver will almost always be better tuned for performance for a specific line of devices vs a more generic driver. When every microsecond matters, you can’t beat them.
For devices you don’t see in the list above, if they are USB Audio Class 2-compliant, they will work with our new in-box low-latency audio driver. Our new driver also provides plug & play compatibility with all USB Audio Class 2 interfaces so that musicians, podcasts, and audio professionals can have a “just works” experience right out of the box.
A year ago, at Snapdragon Summit 2024, Qualcomm announced the new in-box ASIO driver for low-latency audio on Windows. Since that time, we’ve been partnering with Qualcomm and Yamaha to complete the driver work, with Yamaha tapping their years of audio driver development experience to create a great-performing class driver for Windows.
Today, we’re in testing, validation, and bug-fixing mode in preparation for a public preview of the new driver in 2026. Thank you to Qualcomm and Yamaha for the incredible partnership in developing this driver with us.
Opening the In-Box ASIO Driver Repo
Earlier this year, we opened the repo for this driver to make the source available to everyone. We felt that making this source code public, under a permissive MIT license, was the right way to go to help grow the ecosystem of ASIO drivers on Windows.
This driver has been developed by Yamaha Japan, using their hard-won expertise with ASIO and USB Audio Class 2 devices. We’re really excited to have partnered with them and Qualcomm on this project!
Any person or company can now take this code, and with an open source or commercial ASIO license from Steinberg, create their own ASIO drivers, building on the practices followed in our code. Or they can contribute to this driver to help us ensure it remains the best in-box USB audio driver on Windows.
It’s also a great way to see exactly what our driver is doing, and also participate in development to contribute code back to the repo to light up other features or tune performance for devices, power management, new processors, etc. This driver source code is the same source we pull into Windows, and so you can see, just like we did with MIDI 2.0, exactly how everything works. Low-latency audio repo
New Features
Our current in-box USB Audio Class 2 driver, in addition to having higher latency, also doesn’t support some key features that devices need. It doesn’t have both implicit and explicit feedback for example, nor does it support all the audio endpoints a device may surface. And, of course, it doesn’t have a native ASIO driver attached to it.
The new driver fixes all of those deficiencies, and again because of the open source nature, will be even easier for us or partners to extend in the future to support any missing features required by other new devices.
And, of course, the new driver supports both Arm64 and Intel/AMD x64 architectures, so you can use it on your Windows 11 PCs regardless of the CPU you prefer.
Release Plans
We expect to release a public preview of the new driver in 2026 through Windows Insider Canary releases of Windows. We may have to release the ASIO control panel applet separately via GitHub, but are working on the plan for that.
We expect a long public validation cycle with this driver, because there are so many devices we need to ensure backwards compatibility with. These aren’t just musician-focused devices, but also various docks, headphones, DACs, and more.
If you want to participate in this work, our MIDI Discord server is now the MIDI and Audio Discord server, and has specific channels just for the new driver. In addition, for developers, we welcome bug reports in our public repo.
Others
We know there’s a strong desire for other ASIO drivers in Windows as well, including those for on-board low-latency audio, and something to provide aggregation of different audio endpoints. While we do not yet have concrete plans to share there, we recognize both the need and the utility of this for musicians on Windows.
The future is bright
With apps, devices, and important technologies like JUCE and iLok all either already native or coming soon, we know that making music on Windows on Arm will be an excellent experience for everyone, whether in the studio, home, or out.
The post Fall 2025 Windows Musician Technology and Arm64 Update appeared first on Windows MIDI and Music dev.